Multi-factor Authentication

Enhancing Cybersecurity for a Leading Saudi Ministry
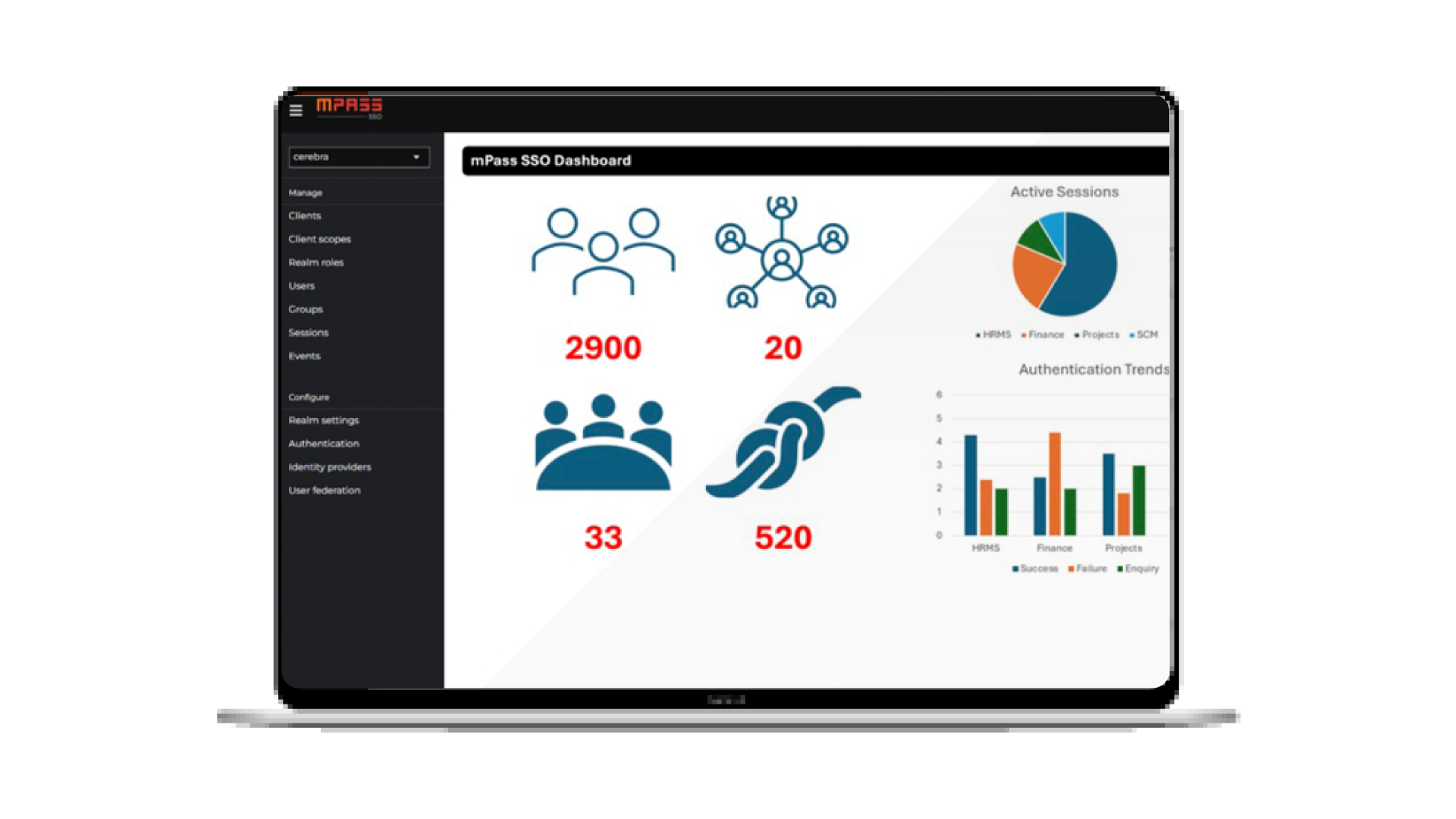
A prominent Saudi Arabian ministry has taken significant steps in its digital transformation journey, focusing on strengthening its cybersecurity framework while aligning with the goals of Vision 2030. In the face of challenges like outdated authentication methods, complex access environments, and strict compliance requirements, the ministry embarked on a two-phase solution to address these issues effectively. Phase One: Implementing Cerebra mPass MFA The first phase of the solution introduced Cerebra mPass Multi-Factor Authentication (MFA), designed to offer a more adaptive, user-friendly approach to authentication. This system enables seamless access controls for users while enhancing security through multiple layers of verification. ...
Read More
Could you be hacked through Slack?
Could you be hacked through Slack? The usage of collaboration platforms such as Microsoft Teams and Slack has significantly increased, with nearly 80% of employees utilizing them. These platforms are designed to be convenient and easily manageable for daily conversations within organizations. However, what makes them easy and convenient also renders them vulnerable to cyber threats and attacks. In 2021, for instance, 780 gigabytes of data from the gaming giant Electronic Arts (EA) were breached through Slack! During the same year, a security vulnerability in Microsoft Teams was exploited to launch a widespread cyber attack on ...
Read More
Push Authentication: A New Era in Multi-Factor Authentication
Want To Say Goodbye To Passwords and OTP Codes? Discover Push Authentication! It is easy for your password to be compromised through phishing attacks, even if it meets the cybersecurity strong password standards and is difficult to predict So we must get to know the technique of Push based Authentication. Some may recommend that you use Multi-Factor Authentication (MFA) to increase your security. Multi-Factor Authentication (MFA): MFA is the process of logging into your account through multiple steps. It requires you to enter more information, not just your password. But there is another obstacle that arises when using such ...
Read More
6 Tips to create a strong password easily!
Create a strong password easily! Today it’s very important to everyone who have an account either on social media or any other websites or services to Create a strong password, because you have to treat your password as your best stuff’s and protect it from others. Learn now the easiest and best tips you have to follow to make a strong password.. What is Password? A password is a string of characters that provides access to a digital system or service. It is a crucial security measure that helps to protect sensitive information from unauthorized access. Passwords can be as simple as a word ...
Read More
What is the role of MFA? |ECC & SAMA Compliance
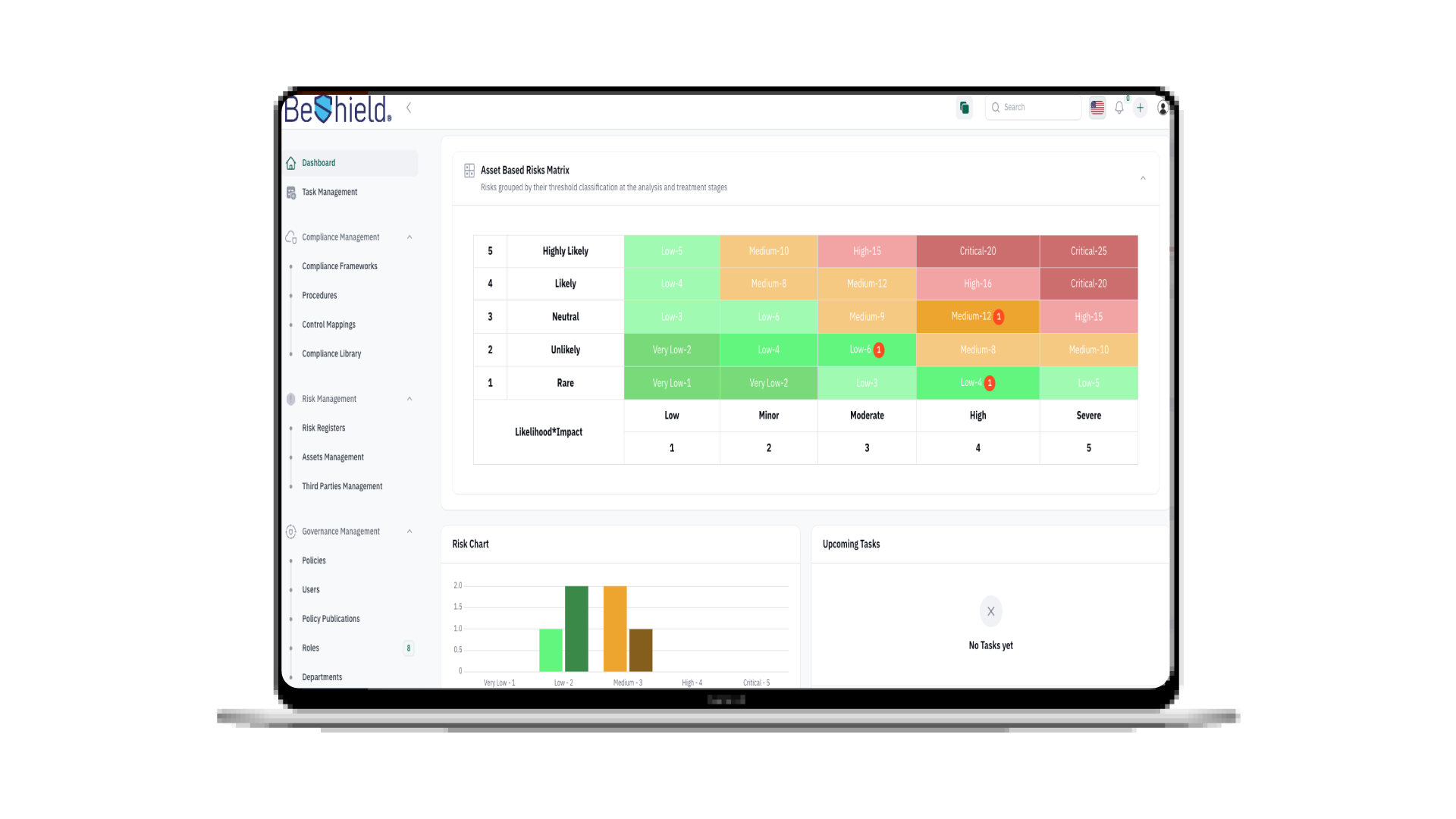
ECC & SAMA Compliance with MFA solution Do you know that there are a great MFA solutions in market today help your organization for ECC & SAMA Compliance? this article will show you how and we will provide you the most incredible MFA solution help to comply with Cybersecurity regulation in KSA.. With the world of cyber threats becoming more intense than ever, organizations need to comprehend the need for an improved cybersecurity framework. The universal goal is to protect the organization’s network from any outsider or insider threats, especially with the addition of remote work resulting from the COVID-19 ...
Read More
Enterprise Messaging Gateway: 2023 Full guideline
Enterprise Messaging Gateway Did you search before about Enterprise Messaging Gateway? this is a full guide to understand What is it? And what are its types? With technology evolving day by day, new developments are being made to align with today’s fast-paced society and especially with remote work culture where we don’t meet people as often as we used to. Any business or organization must take this into consideration to keep up with the current trends. One of the notable evolvements that occurred is the means of communication. The way we communicate with one another changes as technology evolves. Calls, ...
Read More
MFA: the New Firewall In the 21st century
MFA- Multi Factor Authentication This article will help you to understand why Multi Factor Authentication( MFA )became an important architectural component in protecting us in the new Working From Home. Introduction In the early days, Cybersecurity (then called IT Security or information security) used to be merely a username and password. If you ask to someone, they would say I have a username and password so I am safe. It wasn’t much of the internet at that time. Eventually, people have learned that password isn’t sufficient to protect their digital assets. So Antivirus (AV) software flourished and we saw a ...
Read More