Cybersecurity Awareness

Deepfake in Phishing: Challenges and Solutions
In the era of advanced technologies, especially with the explosive adoption of Large Language Models (LLMs) and Generative Artificial Intelligence (GenAI), deepfake has emerged as one of the most significant challenges in cybersecurity. This technology relies on Artificial Intelligence, specifically deep learning and the use of GenAI, to create fake yet highly realistic content that is difficult to detect. Deepfake serves as a versatile tool spanning applications from entertainment to cybersecurity. However, its misuse can pose severe risks, especially in phishing schemes. What is Deepfake? Synthetic media refers to a technology that leverages deep learning algorithms to create ...
Read More
Cyber Warfare Unveiled: Tracing the Journey from Espionage to Digital Combat
“Cyber Warfare: From Espionage to War A Journey Through Time” With the massive technological advancements, the boundaries of warfare have expanded to encompass cyberspace, where “cyber warfare” has emerged as an increasingly serious threat to individuals, institutions, and countries. The line between cyber and traditional wars has blurred for a while but recent activities in the region made it clear that cyberwars is becoming a dangerous and can lead to harming humans. In this blog, we will dive into a journey through the world of cyber warfare, seeking to understand its nature, history, impacts, types, evolution, and some solutions to ...
Read More
Keeping Our Kids Safe Online
A Guide For Keeping Your Kids Safe Online Parents and all who are concerned about the well-being of our young kids in this digital world. Today we will discuss a topic of utmost importance: digital safety for kids. Yes, the Internet can be a very dangerous place for our young kids , especially with the spread of phishing scams. So, let us dive deeper and present to you, in this comprehensive article, a comprehensive guide on digital safety for kids. What every parent needs to pay attention to. Internet risks for kids: The internet has become a big part of ...
Read More
Could you be hacked through Slack?
Could you be hacked through Slack? The usage of collaboration platforms such as Microsoft Teams and Slack has significantly increased, with nearly 80% of employees utilizing them. These platforms are designed to be convenient and easily manageable for daily conversations within organizations. However, what makes them easy and convenient also renders them vulnerable to cyber threats and attacks. In 2021, for instance, 780 gigabytes of data from the gaming giant Electronic Arts (EA) were breached through Slack! During the same year, a security vulnerability in Microsoft Teams was exploited to launch a widespread cyber attack on ...
Read More
Tips To Be Cyber Protected While Traveling
Goodbye worry! A safe journey in the digital world With all the modern wonders of the digital world, we trust communication technologies on our journeys. There is no doubt that the travel experience is always more beautiful and enjoyable, but it can also pose a range of risks, especially when it comes to cybersecurity. Travelers may fall victim to phishing, Wi-Fi network spying, and theft of their personal data, which can make their journey filled with worries and tension. With the increasing prevalence of cyber threats, it is essential for travelers to follow some guidelines to protect their devices and ...
Read More
6 Tips to create a strong password easily!
Create a strong password easily! Today it’s very important to everyone who have an account either on social media or any other websites or services to Create a strong password, because you have to treat your password as your best stuff’s and protect it from others. Learn now the easiest and best tips you have to follow to make a strong password.. What is Password? A password is a string of characters that provides access to a digital system or service. It is a crucial security measure that helps to protect sensitive information from unauthorized access. Passwords can be as simple as a word ...
Read More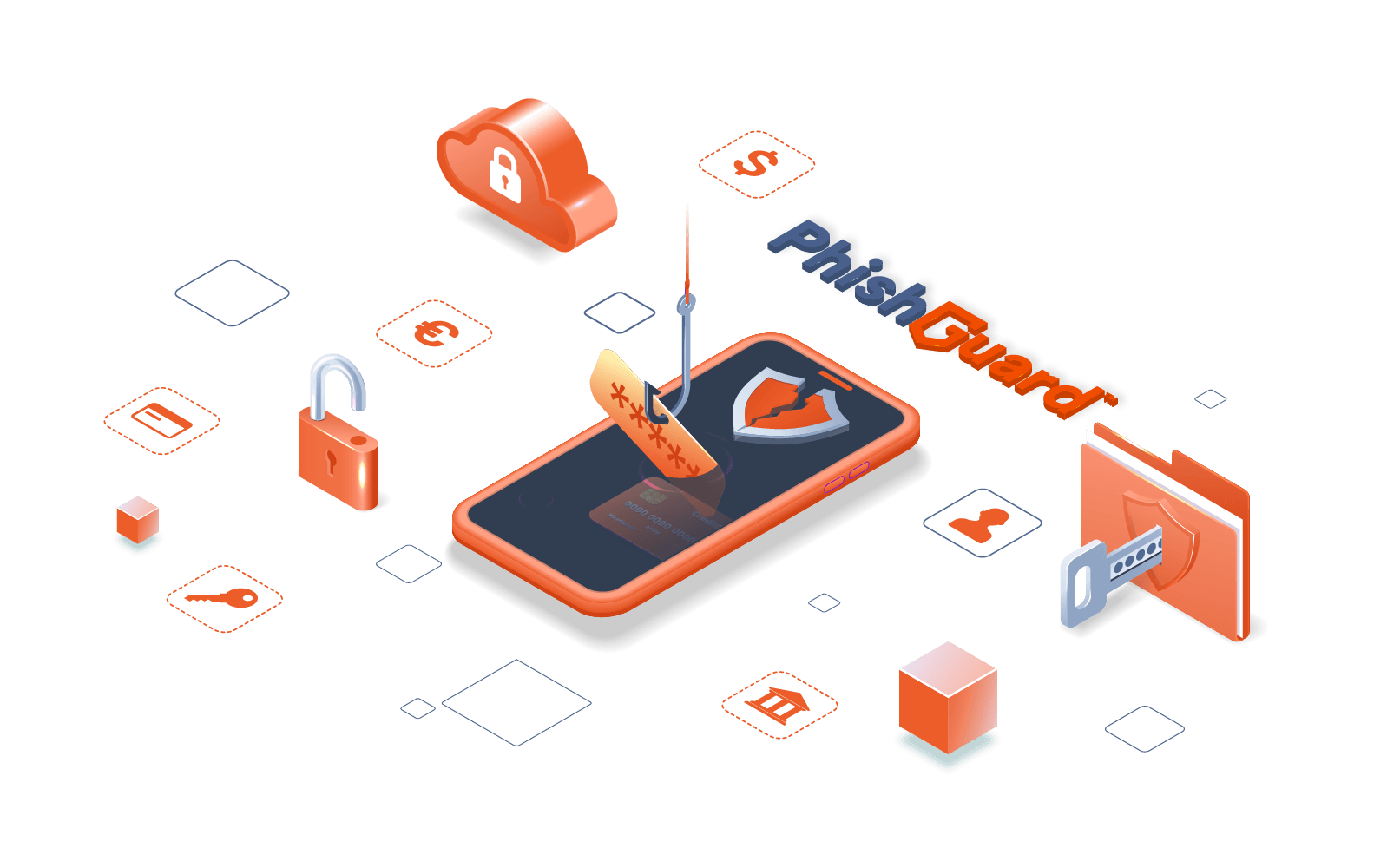
Employees and cyber security: dangerous statistics about Phishing
Employees and cyber security The relationship between employees and cyber security this days must be tight and your company have to give it the right care if you want to keep your data and your business secure.. According to insights from our leading Phishing simulation tool PhishGuard, 58% of users in Saudi Arabia have opened at least one phishing email. These insights reveal that at least one out of four employees have interacted with a phishing email, either by clicking on a link or downloading a malicious attachment. In some cases, employees have gone further and submitted their personal information ...
Read More
Uber security breach by 18-year-old Hacker!
Uber security breach by 18-year-old Hacker! Uber security breach proves that the largest companies can be hacked by teenagers! this news will undoubtedly shock you.. How Uber security breach happened? Uber recently experienced a cyberattack where an 18-year-old hacker accessed their systems by launching a successful social engineering attack on an employee. The hacker used stolen employee credentials to launch an MFA (Multi-Factor authentication) Fatigue attack. It is an attack where a victim receives multiple requests from their MFA application till it bothers them out leading them to eventually accept the request. The teenage attacker did not disclose how he ...
Read More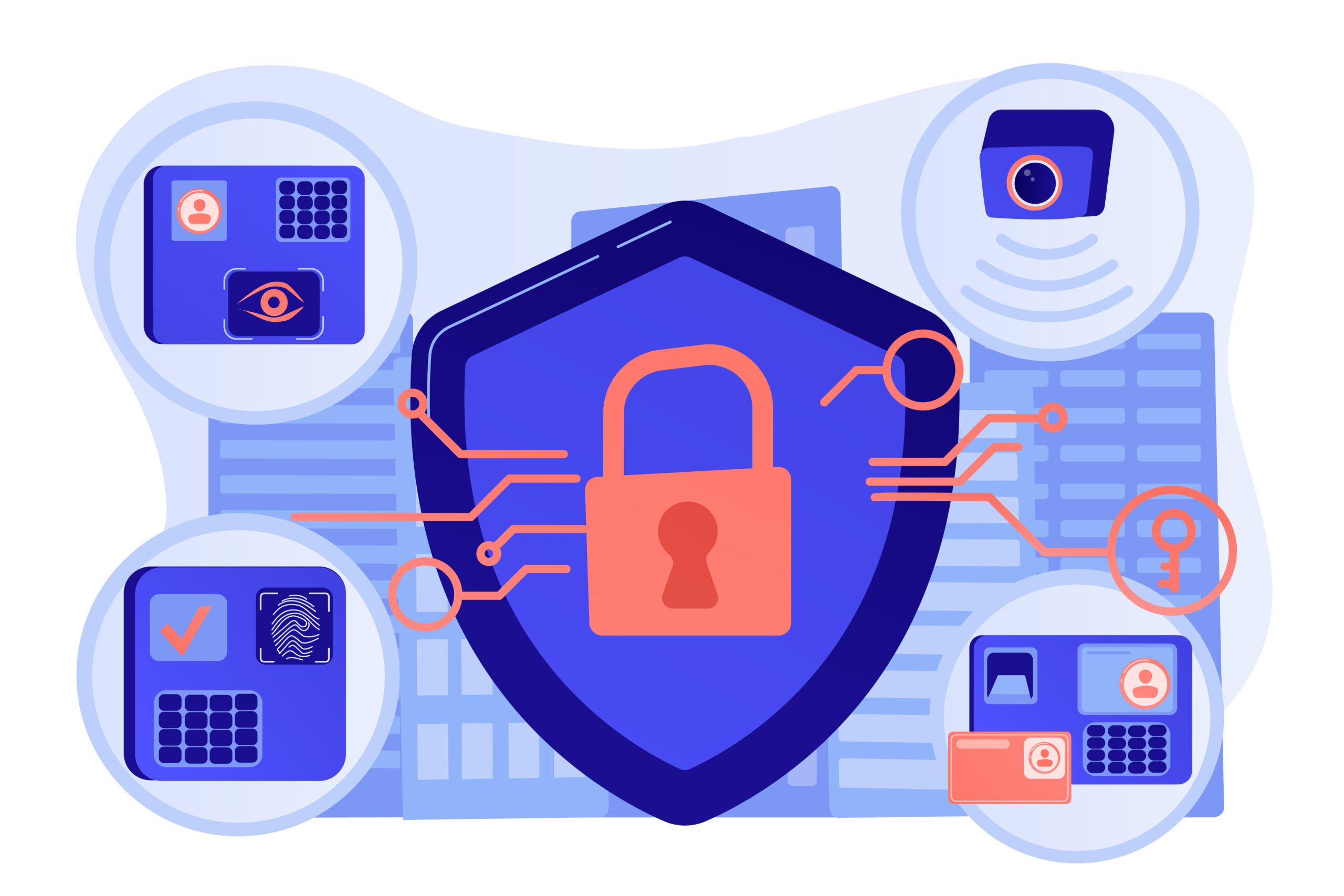
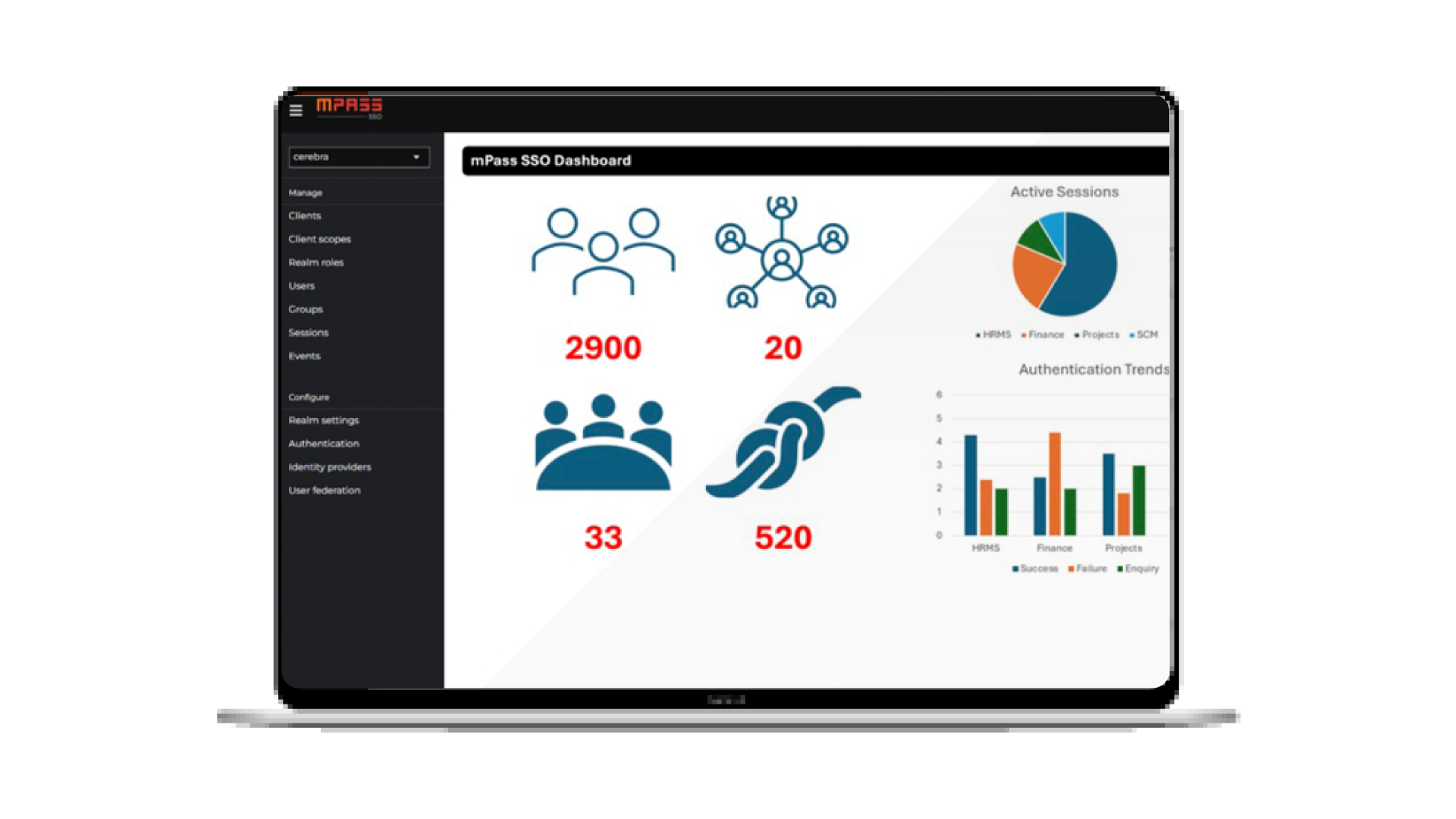
Identity Access Management (IAM) | What is it?
Identity Access Management (IAM) It’s so important for organizations today to Identity Access management solution. This article will put your org on the right direction! With Digital Transformation, remote work acceptance and e-services becoming ubiquitous, Businesses’ and organizations – of all sizes – main concern is to keep its Information Technology (IT) up and running around the clock. This requires its various ingredients such as database and servers to be secure. This means they are always on the lookout for ways to achieve the most efficient way to be safe and secure. Typically, organizations follow basic protocols and use p asswords ...
Read More- 1
- 2