Secured by Innovation
Cerebra, is a software products company that develops next-generation cybersecurity technologies, based in Riyadh, Kingdom of Saudi Arabia.
Learn MoreABOUT US
Brief about the company
Cerebra is software products company that engages in the design and development of next-generation cybersecurity technologies headquartered in Riyadh, Kingdom of Saudi Arabia.
Our quest is to achieve Cybersecurity Technology Independence across the Gulf Cooperation Council (GCC) region, to transform the region from a Passive Cybersecurity Technology Consumer to a Dynamic and Futuristic Cybersecurity Technology Producer, in order help protect against modern-day malicious actors in the cyberspace. Our quest is also to align and contribute towards the realization of the Kingdom’s Vision 2030.

OUR PRODUCTS
Products Brief
is a powerful enterprise messaging gateway and communication platform that enables systems and applications to send and receive messages through SMS, Email or Mobile Push Notifications.
is a multi-factor authentication solution that provides better security for any organization looking to protect its employees from fraud attacks, phishing, and password related attacks.
Read More
is a comprehensive cybersecurity awareness platform that aims to spread knowledge about the fundamental concepts of cybersecurity.
Read More
is a comprehensive phishing simulation solution that aims to raise the level of security awareness of your employees on various phishing scams.
Read More
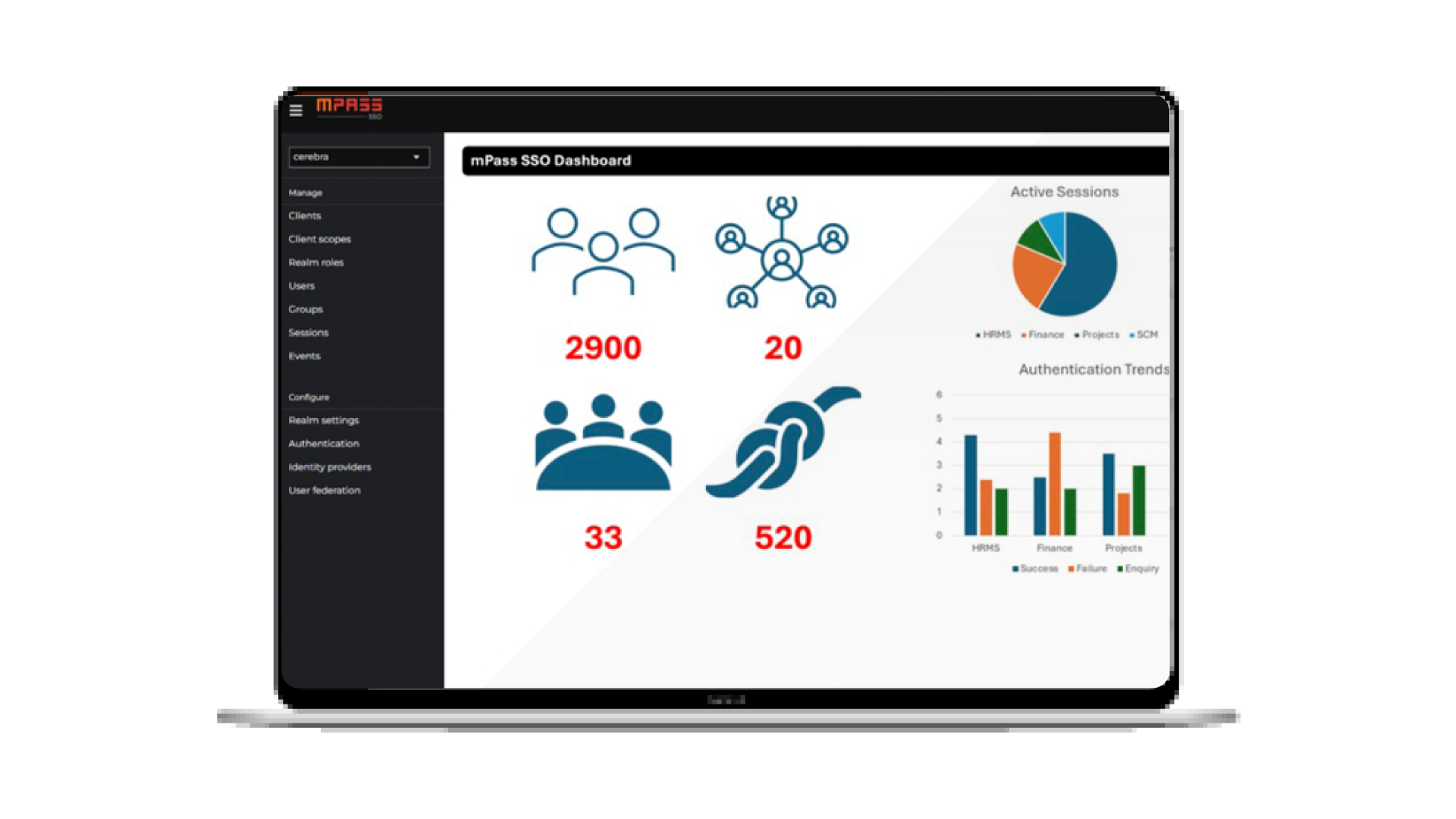
The modern single sign-on (SSO) platform increases productivity by enabling users to access multiple applications or services using just one set of strong login credentials.
Read More
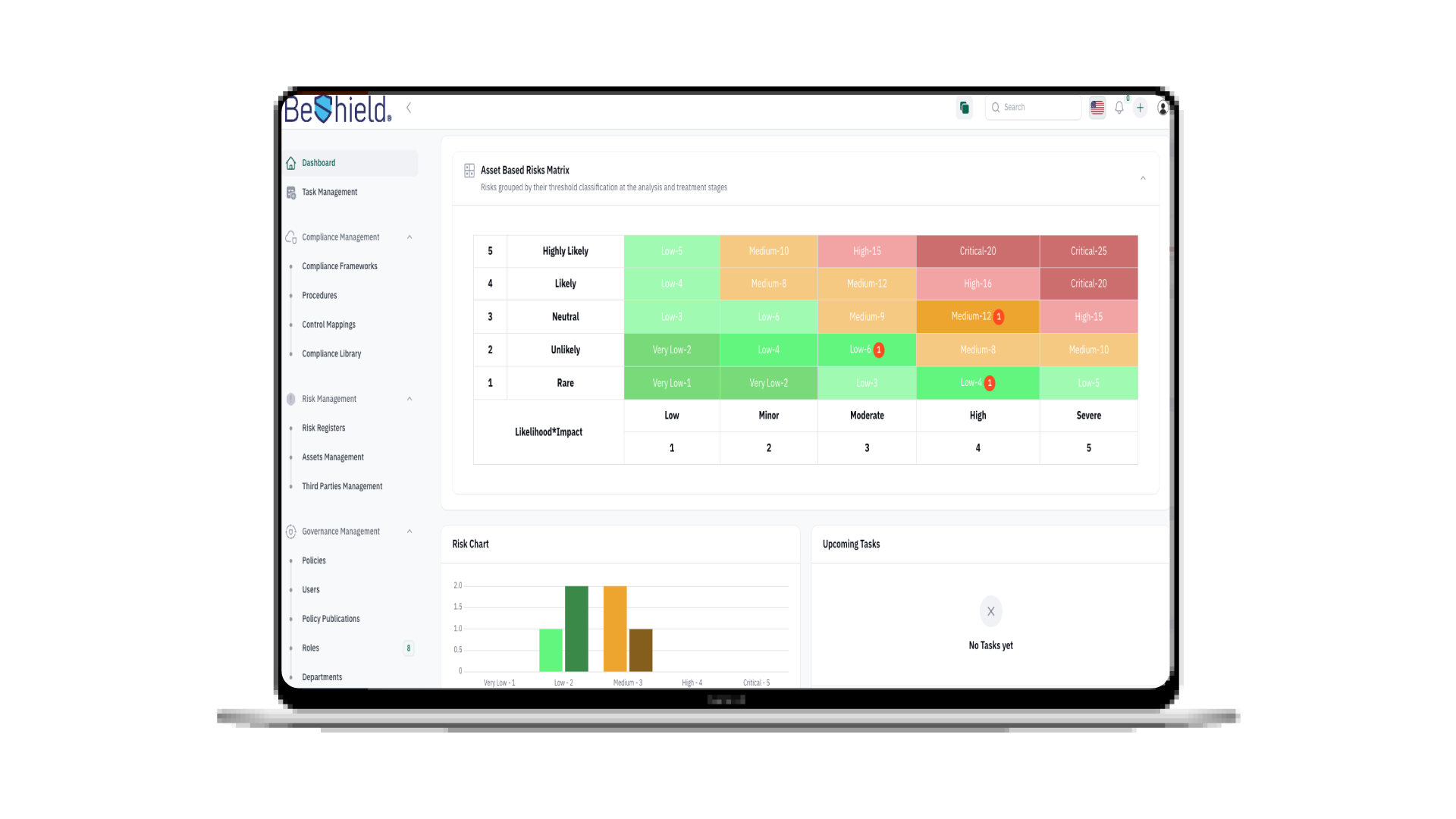
BeShield streamlines compliance processes, enhances decision-making, and safeguards your business's integrity with intuitive monitoring and regulatory adherence.
Read More
TESTIMONIALS
What our clients say about us

+Aware User
Cybersecurity Department
We recently collaborated with Cerebra for our cybersecurity awareness campaign, and it truly exceeded our expectations. Their team was not only professional and knowledgeable, but also incredibly engaging. They expertly tailored the content to meet our organization’s needs, making complex topics accessible and relevant to all employees. The interactive sessions and real-life scenarios not only informed but also empowered our staff to take cybersecurity seriously. Since the campaign, we’ve seen a remarkable increase in awareness and proactive behaviors regarding cybersecurity practices within our organization.
Infoshield User
GRC Consultant
We recently collaborated with Cerebra for a cybersecurity awareness campaign using Infoshield, and it exceeded our expectations. The platform was easy to use, and the content was both relevant and engaging for our employees. It presented complex cybersecurity topics in a clear, accessible way that resonated across all levels of our organization.The interactive modules and real-life scenarios within Infoshield didn’t just inform—they inspired our staff to take cybersecurity seriously. Since rolling it out, we’ve noticed a significant improvement in awareness and more proactive cybersecurity behavior throughout the company

Infoshield User
Human Resources Development Fund
Infoshield is an intuitive, user-friendly, and powerful platform helped us to improve our awareness cutlers. The admin console and end-user localization options support multiple languages for more immersive learning experience.
Infoshield User
King Abdulaziz Royal Reserve Development Authority
I have been using Infoshield for quite some time now, and I must say it has completely transformed the users approach of cybersecurity awareness. It's a powerful, user-friendly, and comprehensive platform that caters to all users. I highly recommend Infoshield to anyone seeking to enhance their cybersecurity educational experience. Furthermore, the support and customer service provided by CEREBRA are second to none. Any questions or issues I've had were promptly addressed.

Hisham Khan
Cybersecurity Manager - Makkah Region Development Authority
Infoshield has been a game-changer for MRDA cyber security awareness maturity level. This tool has made it incredibly easy for us to educate and empower our employee's knowledge. Its user-friendly interface and engaging content have significantly enhanced their awareness of potential threats, helping them become our first line of defense against cyberattacks.
PhishGuard User
Cybersecurity Manager
Using PhishGuard has been a game-changer for our cybersecurity training. It's user-friendly, offers realistic simulations, and helps us pinpoint areas for improvement in employee awareness. This tool is essential in today's evolving threat landscape, and I highly recommend it.
Deena Gashgarey
Assistant Cybersecurity Manager - Red Sea Global
Cerebra offers great solutions and excellent customer support, and one of the unique solutions offered is PhishGuard. I am very pleased with the level of professionalism and support offered by Cerebra.
Infoshield User
Cyber Security Development Manager
The InfoShield Learning Management system is very user-friendly, and it significantly improved our current training process. The most impressive to us was the LMS, and customer service. Cerebra team was instrumental during the implementation of InfoShield for our company, and during the integration phase with our new LMS. They were very quick to answer any questions we had and helped us with any issues we ran into during integration. I would recommend Cerebra’s InfoShield, and PhishGuard to any company that is looking for web-based Learning Management Solutions for their Cybersecurity awareness program.

Khaled Alsulaimi
Senior Cybersecurity Manager
PhishGuard is an amazing phishing simulation solution that enables a Cybersecurity team to properly test the level of awareness for an organization. It's accompanied with a great support team and is constantly being enhanced with new updates and functionalities.
Mohammed K. AlDhahri
Al Nefaie Investment Group
I would like to express our sincere appreciation for your service to us that you have provided the highest quality cyber security products local in KSA with even better customer service.
LATEST ARTICLES
Deep dive in the cyber world
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means A massive data leak came to light on October 28, 2025, with reports confirming that hundreds of millions of user credentials have been exposed online. Below, we break down the key facts of this breach – including its source, scale, and implications – and then explore how cybersecurity solutions from Cerebra.sa could help prevent or mitigate such incidents in the future. Overview of the October 28, 2025 Data Leak Source/Target: The breach did not stem from a single company hack, but rather from a trove ...
Read More
Top 3 Phishing Types and How to Prevent Them in 2025
Phishing Types: Spear Phishing, Smishing & How to Avoid Phishing Emails The Enduring Threat: Why Phishing Attacks Are Getting Smarter Phishing types like spear phishing, smishing, and whaling are becoming more sophisticated in 2025, making it harder than ever to avoid phishing emails. This guide explores the most dangerous phishing types and shows you how to recognize and prevent them before they cause harm. The National Cybersecurity Authority (NCA) reinforces this urgency with its awareness message: ‘Stop for 5 seconds… Guard Your Cyberspace.’ What Is Phishing? Definition and Modern Tactics Phishing is a cyberattack where malicious actors impersonate trusted ...
Read More
5 Critical Benefits of AI in Cybersecurity: Latest Data and Threat Defense in 2025
Using AI in Cybersecurity We should start learning using AI in cyber security because Hackers aren’t going to slow down any time soon and with a using AI! The next step to level up in protecting your business’s IT infrastructure is to integrate artificial intelligence. Studies have revealed that AI will strengthen the wall between systems and cyber threats. According to an IBM report, the global average cost of a data breach in 2025 is $4.4 million. Even though, it decreased by 9% vs previous year, the numbers are still way higher than few years back. They are elevating their approaches ...
Read More
6 benefits of SMS Marketing you should know!
6 benefits of SMS Marketing you should know! Have you ever used SMS marketing to reach and communicate with your audience, if not! I’m sure that you will change your mind when you read about the benefits of SMS Marketing, continue this article to learn.. Many businesses are constantly seeking ways to interact with and attract new customers. Their joint objective is to reach a wider audience. To do so, communication is key. There are many ways for businesses to communicate with their audience, either by email, social media, or adverts, but the most beneficial marketing method, that is often ...
Read More
MFA: the New Firewall In the 21st century
MFA- Multi Factor Authentication This article will help you to understand why Multi Factor Authentication( MFA )became an important architectural component in protecting us in the new Working From Home. Introduction In the early days, Cybersecurity (then called IT Security or information security) used to be merely a username and password. If you ask to someone, they would say I have a username and password so I am safe. It wasn’t much of the internet at that time. Eventually, people have learned that password isn’t sufficient to protect their digital assets. So Antivirus (AV) software flourished and we saw a ...
Read More
What is the role of MFA? |ECC & SAMA Compliance
ECC & SAMA Compliance with MFA solution Do you know that there are a great MFA solutions in market today help your organization for ECC & SAMA Compliance? this article will show you how and we will provide you the most incredible MFA solution help to comply with Cybersecurity regulation in KSA.. With the world of cyber threats becoming more intense than ever, organizations need to comprehend the need for an improved cybersecurity framework. The universal goal is to protect the organization’s network from any outsider or insider threats, especially with the addition of remote work resulting from the COVID-19 ...
Read More
The AI Revolution in Cybersecurity: A New Frontier of Defense
The AI Revolution in Cybersecurity: A New Frontier of Defense How is AI revolutionizing the cybersecurity industry? The rapid evolution of Artificial Intelligence (AI), especially with the rise of Generative AI (GenAI), is not just reshaping every industry; it is fundamentally transforming how we approach digital defense. As cyber threats grow in complexity and scale, AI is emerging as a powerful ally, offering innovative solutions to protect digital assets and infrastructure. For a full list of advantages, read about the 5 Benefits of Using AI in Cyber security. At Cerebra, we explore how AI is reshaping the cybersecurity landscape—from enhancing ...
Read More
Uber security breach by 18-year-old Hacker!
Uber security breach by 18-year-old Hacker! Uber security breach proves that the largest companies can be hacked by teenagers! this news will undoubtedly shock you.. How Uber security breach happened? Uber recently experienced a cyberattack where an 18-year-old hacker accessed their systems by launching a successful social engineering attack on an employee. The hacker used stolen employee credentials to launch an MFA (Multi-Factor authentication) Fatigue attack. It is an attack where a victim receives multiple requests from their MFA application till it bothers them out leading them to eventually accept the request. The teenage attacker did not disclose how he ...
Read More
Biometric Authentication: Is it reliable?
Biometric Authentication The history of bio-metrics used as an authentication tool dates to the 1800s. It was first used by the French to identify criminals through their fingerprints, which later the English police commissioner, Edward Henry, developed HCS “Henry Classification System”. It was a system that relied on fingerprints to identify people who have been prosecuted, it was a prime way of classification used by the police during the 20th century. As the years continued, new biological traits started being used in biometric authentication which in result are replacing traditional methods of authentication. Any invention introduced in the cyber world ...
Read More
6 Tips to create a strong password easily!
Create a strong password easily! Today it’s very important to everyone who have an account either on social media or any other websites or services to Create a strong password, because you have to treat your password as your best stuff’s and protect it from others. Learn now the easiest and best tips you have to follow to make a strong password.. What is Password? A password is a string of characters that provides access to a digital system or service. It is a crucial security measure that helps to protect sensitive information from unauthorized access. Passwords can be as simple as a word ...
Read MoreOur Clients