Phishing

Deepfake in Phishing: Challenges and Solutions
In the era of advanced technologies, especially with the explosive adoption of Large Language Models (LLMs) and Generative Artificial Intelligence (GenAI), deepfake has emerged as one of the most significant challenges in cybersecurity. This technology relies on Artificial Intelligence, specifically deep learning and the use of GenAI, to create fake yet highly realistic content that is difficult to detect. Deepfake serves as a versatile tool spanning applications from entertainment to cybersecurity. However, its misuse can pose severe risks, especially in phishing schemes. What is Deepfake? Synthetic media refers to a technology that leverages deep learning algorithms to create ...
Read More
The Difference Between Phishing Attacks
The Difference Between Phishing Attacks Phishing attacks are harmful attacks used by criminals to steal personal and financial information from individuals and businesses. Attacks on individuals and businesses are becoming more common as we use the internet and technology more often in our daily lives. Phishing attacks involve the use of dishonesty and fraudulent methods to fool consumers into believing they are interacting with the trustworthiness of an unsuspecting destination, such as banks, email companies, or social media platforms. But what is the difference between phishing attacks? How can individuals and organizations protect themselves from such attacks? That is what ...
Read More
Understanding of the Vishing Meaning
Understanding of the Vishing Meaning Vishing, a combination of “voice” and “phishing,” is a sophisticated form of cybercrime that exploits voice communication to trick individuals and extract sensitive information. In this comprehensive guide, we will explore the meaning of it, the dangers associated with it, and effective methods to protect yourself against these malicious attacks. What is Vishing meaning? Vishing refers to the fraudulent practice of using telephone services to trick individuals into revealing personal and financial information. Scammers often pose as trusted organizations or individuals to gain their victims’ trust. By using social engineering tactics and manipulating ...
Read More
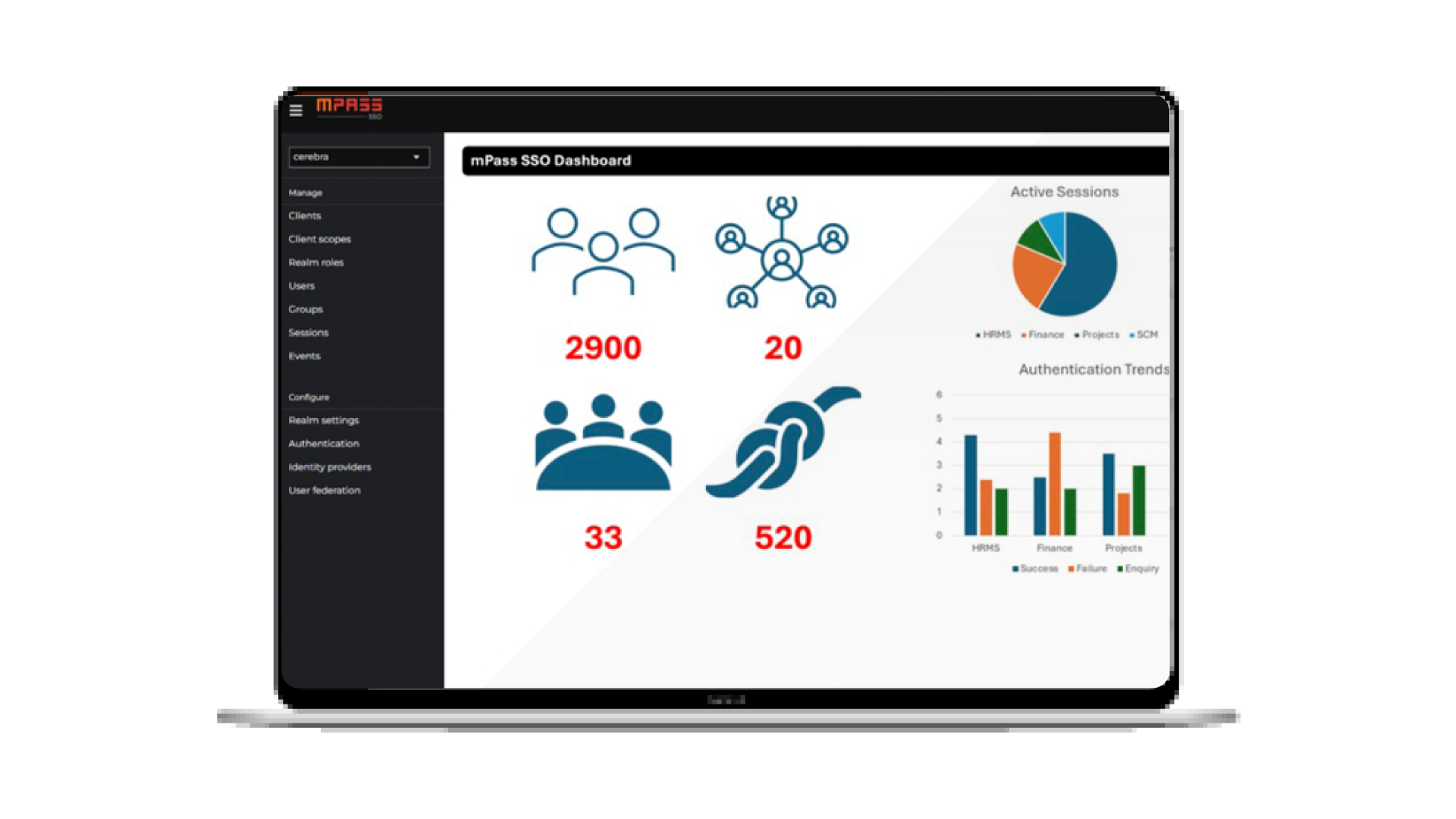
Employees and cyber security: dangerous statistics about Phishing
Employees and cyber security The relationship between employees and cyber security this days must be tight and your company have to give it the right care if you want to keep your data and your business secure.. According to insights from our leading Phishing simulation tool PhishGuard, 58% of users in Saudi Arabia have opened at least one phishing email. These insights reveal that at least one out of four employees have interacted with a phishing email, either by clicking on a link or downloading a malicious attachment. In some cases, employees have gone further and submitted their personal information ...
Read More
Uber security breach by 18-year-old Hacker!
Uber security breach by 18-year-old Hacker! Uber security breach proves that the largest companies can be hacked by teenagers! this news will undoubtedly shock you.. How Uber security breach happened? Uber recently experienced a cyberattack where an 18-year-old hacker accessed their systems by launching a successful social engineering attack on an employee. The hacker used stolen employee credentials to launch an MFA (Multi-Factor authentication) Fatigue attack. It is an attack where a victim receives multiple requests from their MFA application till it bothers them out leading them to eventually accept the request. The teenage attacker did not disclose how he ...
Read More
Smishing Attacks (SMS Phishing) Trends | 2022
Did you know that there are 6.648 billion (83.72%) people worldwide who own a mobile phone and in Saudi Arabia alone, 97.5% of its society owns one? Also, did you know that the average time people spend on their phones is 3 hours and 43 minutes? What if you knew that they are all vulnerable to fraud attacks via Smishing! With most of the world connected to their mobile phones on a daily basis, this incited cyber criminals to level up their SMS phishing attacks . Smishing Attacks Trends It’s no wonder that the number of smishing attacks has increased in the ...
Read More
The 6 hacker hat colors | Explained
hacker hat colors | Explained There are different hacker hat colors: black, white, grey, white, green, and blue hats. this article will explain you the deference.. When the word hacker or hacking is mentioned, a universal definition pops into mind. A hacker is known to be a cybercriminal who inflicts chaos on their victims by breaching, stealing, or damaging online systems and data. This is just one part of what the word hacking withholds. And contrary to popular belief, hacking is a broad and diversified category that is misunderstood. The dependency on storing data electronically, as computers have taken ...
Read More
Insider Threats in Cyber Security | types & protection
Insider Threats in Cyber Security Organizations tend to only focus on setting cyber security measures for potential threats and intrusions made by external circumstances. Unfortunately, they undermine the possibilities of a trusted employee launching a cyber-attack against them. This negligence resulted in 34% of businesses being affected by an insider threat on a yearly basis. This cyber security risk does not only leave the organization vulnerable but is also viewed as an easy target for internal and external threats. Whoever has authorized access to sensitive data, either it being an employee or a partner (which sometimes referred to as Third-party ...
Read More
Juice Jacking: The Threats of Public USB Charging Stations
Juice Jacking and charging in public places Have you ever heard about juice jacking attack? what is it? how it’s happened? and how to protect from it? A shared scenario between many is being in public with a dying mobile device, franticly looking for a charger. When coincidently you find a free charging station calling out your name. You find a solution, but have you ever thought about the risks of using these public charging stations? The accessibility of these public USB charging stations is convenient but connecting your device to one can put you in a vulnerable position. With just plugging in your smartphone or ...
Read More- 1
- 2