Want To Say Goodbye To Passwords and OTP Codes?
Discover Push Authentication!
It is easy for your password to be compromised through phishing attacks, even if it meets the cybersecurity strong password standards and is difficult to predict So we must get to know the technique of Push based Authentication.
Some may recommend that you use Multi-Factor Authentication (MFA) to increase your security.
Multi-Factor Authentication (MFA):
MFA is the process of logging into your account through multiple steps.
It requires you to enter more information, not just your password.
But there is another obstacle that arises when using such technology.
When logging in to any application or website, you must fill in a One-Time-Passcode (OTP) code sent to your mobile phone or email.
True, this will increase the level of security, but at the same time, it will make the process much longer.
It consumes more time!
You must enter the OTP code correctly, and if you make a mistake, the website will re-send the OTP code again, and then you must enter it a second time.
You could have a problem with the email or SMS, so you will not be able to see the OTP code in the first place.
Is there another solution that combines ease of use while increasing security?
Come with us to learn about Push based Authentication technology.
What is it?
How does it work?
What are its special features?
Is it safer?
Learn About Push based Authentication.
Push based Authentication is one of the types of Multi-Factor Authentication (MFA).
It works by sending a notification to the user’s previously registered mobile phone, where the user can then click on the notification to agree or reject the login (Yes / No).
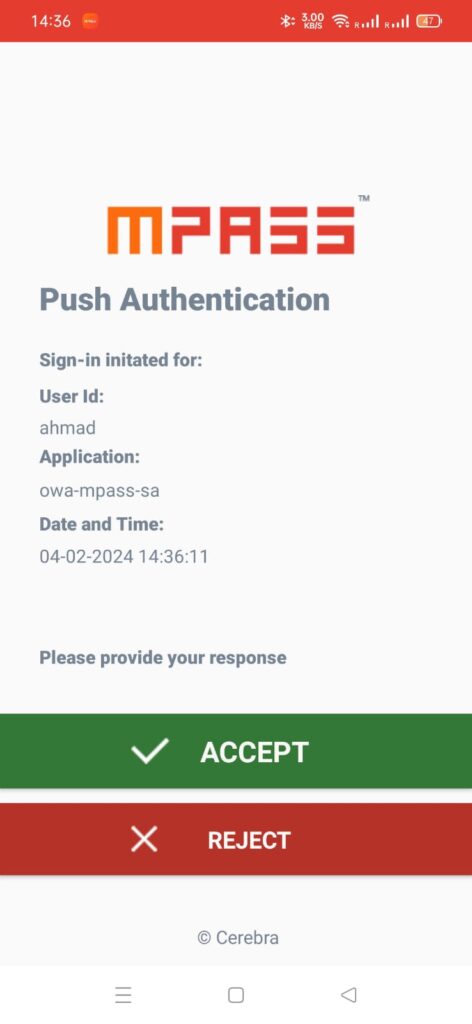
And it adds an extra layer of security by verifying that the user owns the mobile phone to which the notification was sent. Without access to the mobile device, an attacker cannot log in and hack into the account.
Push based Authentication is user-friendly, unlike other types of multi factor authentication solutions.
It only requires the user to approve or reject the request submitted to him/her without the need to a password or enter a security code, such as a One-Time Password (OTP).
Is The Security Level Sufficient?
Some may expect that Push Authentication is not completely secure, and this belief is due to its ease of use, which some people think might reduce the level of security.
But on the contrary, Push Authentication offers us a more secure method than other traditional methods related to MFA.
Push Authentication uses a fully encrypted communication method between the application and the user’s device, providing protection against Man in The Middle Attacks.
Push Authentication is also based on the Out of Band Authentication method, which means that the user’s mobile must be connected to the Internet to receive the notification, which helps to prevent unauthorized access attempts when the user is not connected to the Internet.
Are You Ready To Join The Push Era?
If you are looking to protect your employees and organization from Phishing and password-related attacks, our mPass product, specifically designed with Multi-Factor Authentication technology, offers full support and compliance with international standards for open authentication (OATH).
mPass integrates with most applications and systems and supports combining different methods for providing additional factors and passwords.
Special settings can also be set in many ways, such as SMS, soft tokens and Push based authentication features.
mPass has many uses, as it works to secure access to the company’s virtual network (VPN) for employees who work remotely, and it also works to secure the services companies provide through websites, among many other features.
Learn more about mPass from Cerebra
Share this article:
Popular
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means A massive data leak came to light on October 28, 2025, with reports confirming that hundreds of millions of user credentials have been exposed online. Below, we break down the key facts of this breach – including its source, scale, and implications – and then explore how cybersecurity solutions from Cerebra.sa could help prevent or mitigate such incidents in the future. Overview of the October 28, 2025 Data Leak Source/Target: The breach did not stem from a single company hack, but rather from a trove ...
29th Oct 2025
Top 3 Phishing Types and How to Prevent Them in 2025
Phishing Types: Spear Phishing, Smishing & How to Avoid Phishing Emails The Enduring Threat: Why Phishing Attacks Are Getting Smarter Phishing types like spear phishing, smishing, and whaling are becoming more sophisticated in 2025, making it harder than ever to avoid phishing emails. This guide explores the most dangerous phishing types and shows you how to recognize and prevent them before they cause harm. The National Cybersecurity Authority (NCA) reinforces this urgency with its awareness message: ‘Stop for 5 seconds… Guard Your Cyberspace.’ What Is Phishing? Definition and Modern Tactics Phishing is a cyberattack where malicious actors impersonate trusted ...
5th Aug 2025
5 Critical Benefits of AI in Cybersecurity: Latest Data and Threat Defense in 2025
Using AI in Cybersecurity We should start learning using AI in cyber security because Hackers aren’t going to slow down any time soon and with a using AI! The next step to level up in protecting your business’s IT infrastructure is to integrate artificial intelligence. Studies have revealed that AI will strengthen the wall between systems and cyber threats. According to an IBM report, the global average cost of a data breach in 2025 is $4.4 million. Even though, it decreased by 9% vs previous year, the numbers are still way higher than few years back. They are elevating their approaches ...
1st Aug 2025
6 benefits of SMS Marketing you should know!
6 benefits of SMS Marketing you should know! Have you ever used SMS marketing to reach and communicate with your audience, if not! I’m sure that you will change your mind when you read about the benefits of SMS Marketing, continue this article to learn.. Many businesses are constantly seeking ways to interact with and attract new customers. Their joint objective is to reach a wider audience. To do so, communication is key. There are many ways for businesses to communicate with their audience, either by email, social media, or adverts, but the most beneficial marketing method, that is often ...
30th Jul 2025
MFA: the New Firewall In the 21st century
MFA- Multi Factor Authentication This article will help you to understand why Multi Factor Authentication( MFA )became an important architectural component in protecting us in the new Working From Home. Introduction In the early days, Cybersecurity (then called IT Security or information security) used to be merely a username and password. If you ask to someone, they would say I have a username and password so I am safe. It wasn’t much of the internet at that time. Eventually, people have learned that password isn’t sufficient to protect their digital assets. So Antivirus (AV) software flourished and we saw a ...
20th Jul 2025
What is the role of MFA? |ECC & SAMA Compliance
ECC & SAMA Compliance with MFA solution Do you know that there are a great MFA solutions in market today help your organization for ECC & SAMA Compliance? this article will show you how and we will provide you the most incredible MFA solution help to comply with Cybersecurity regulation in KSA.. With the world of cyber threats becoming more intense than ever, organizations need to comprehend the need for an improved cybersecurity framework. The universal goal is to protect the organization’s network from any outsider or insider threats, especially with the addition of remote work resulting from the COVID-19 ...
15th Jul 2025
The AI Revolution in Cybersecurity: A New Frontier of Defense
The AI Revolution in Cybersecurity: A New Frontier of Defense How is AI revolutionizing the cybersecurity industry? The rapid evolution of Artificial Intelligence (AI), especially with the rise of Generative AI (GenAI), is not just reshaping every industry; it is fundamentally transforming how we approach digital defense. As cyber threats grow in complexity and scale, AI is emerging as a powerful ally, offering innovative solutions to protect digital assets and infrastructure. For a full list of advantages, read about the 5 Benefits of Using AI in Cyber security. At Cerebra, we explore how AI is reshaping the cybersecurity landscape—from enhancing ...
6th Jul 2025
Uber security breach by 18-year-old Hacker!
Uber security breach by 18-year-old Hacker! Uber security breach proves that the largest companies can be hacked by teenagers! this news will undoubtedly shock you.. How Uber security breach happened? Uber recently experienced a cyberattack where an 18-year-old hacker accessed their systems by launching a successful social engineering attack on an employee. The hacker used stolen employee credentials to launch an MFA (Multi-Factor authentication) Fatigue attack. It is an attack where a victim receives multiple requests from their MFA application till it bothers them out leading them to eventually accept the request. The teenage attacker did not disclose how he ...
15th Jun 2025
Biometric Authentication: Is it reliable?
Biometric Authentication The history of bio-metrics used as an authentication tool dates to the 1800s. It was first used by the French to identify criminals through their fingerprints, which later the English police commissioner, Edward Henry, developed HCS “Henry Classification System”. It was a system that relied on fingerprints to identify people who have been prosecuted, it was a prime way of classification used by the police during the 20th century. As the years continued, new biological traits started being used in biometric authentication which in result are replacing traditional methods of authentication. Any invention introduced in the cyber world ...
10th Jun 2025