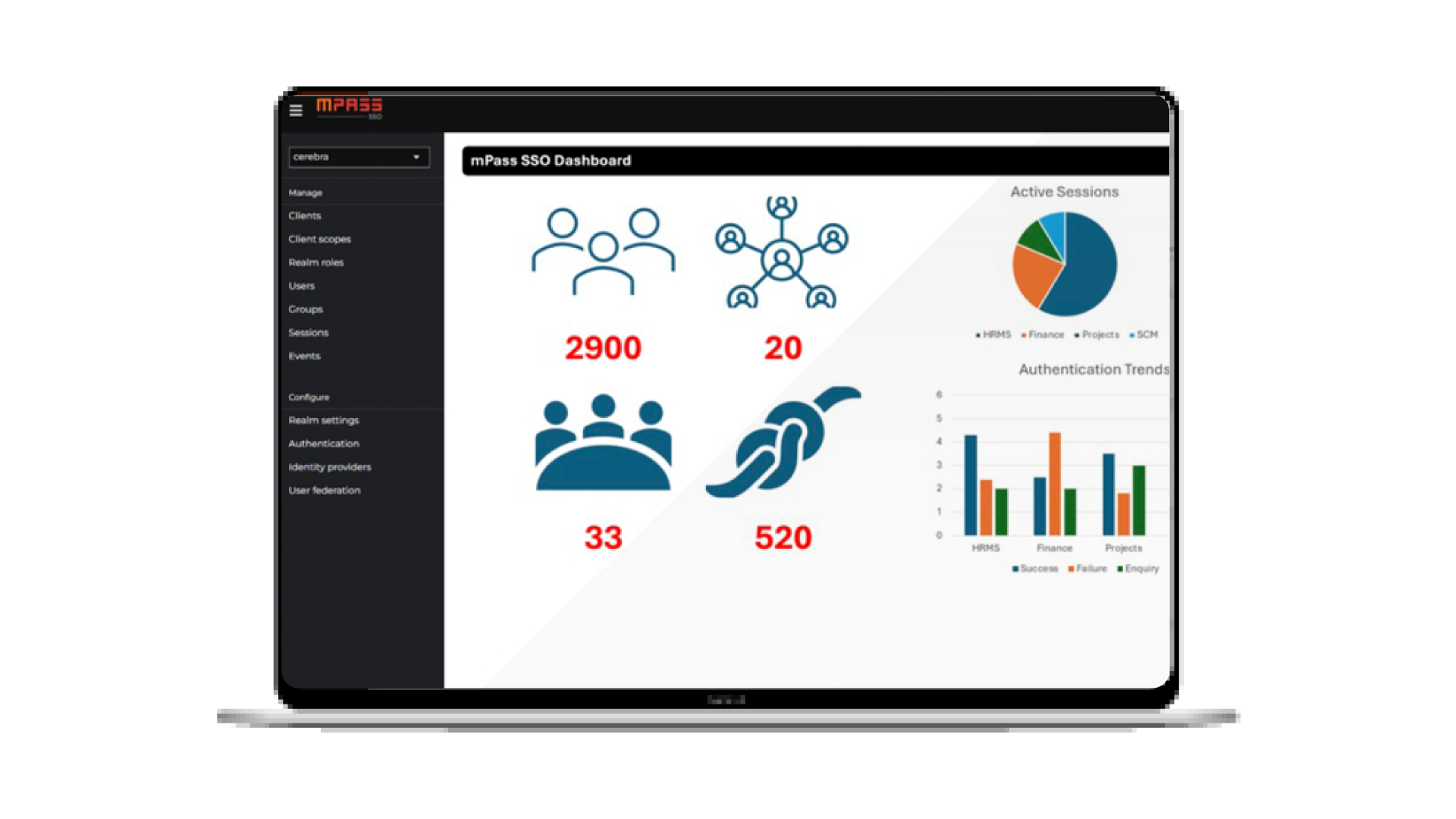
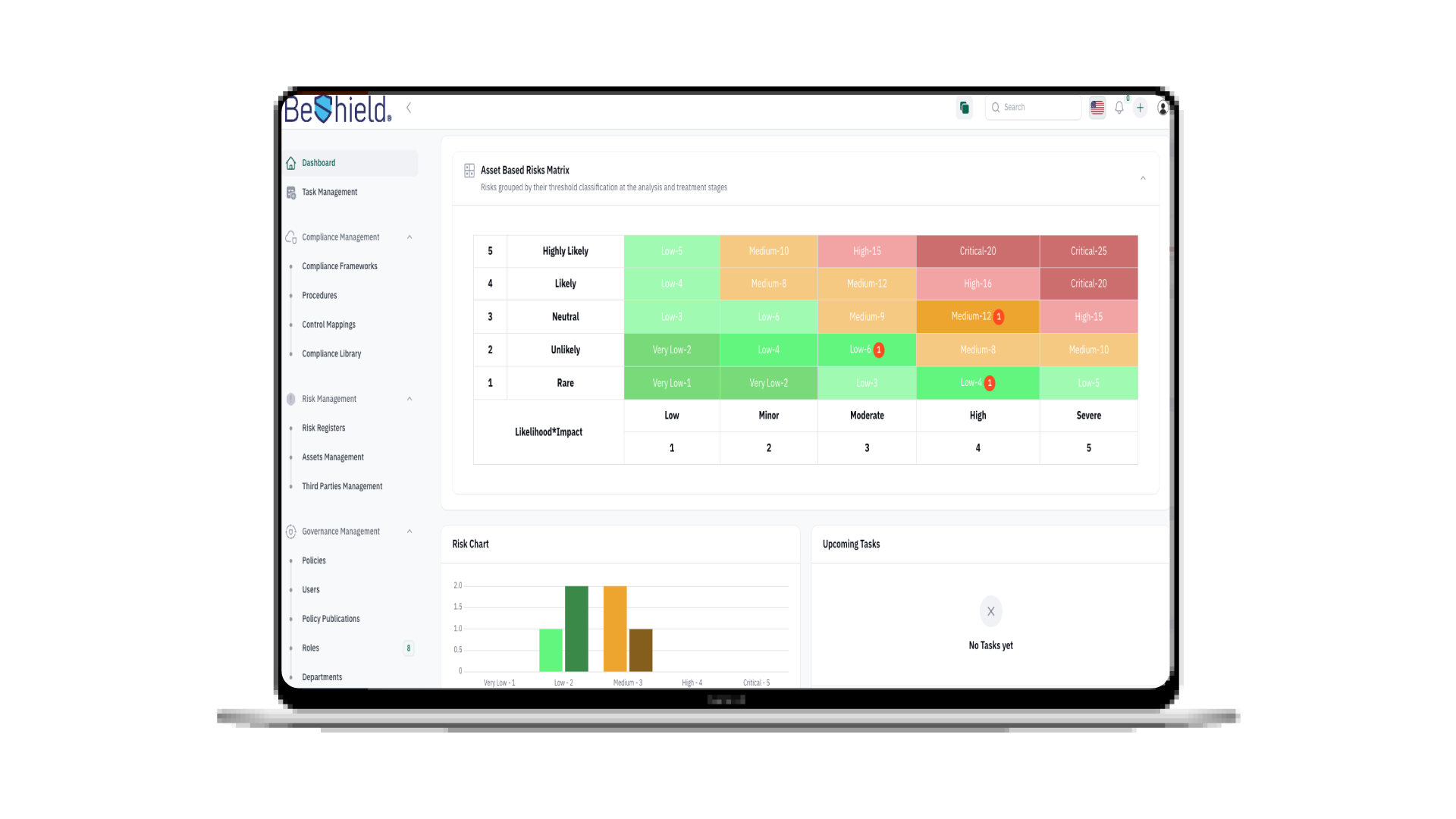
The AI Revolution in Cybersecurity: A New Frontier of Defense
The rapid evolution of Artificial Intelligence (AI), especially with the rise of Generative AI (GenAI), is reshaping every industry, and cybersecurity is no exception. As cyber threats grow in complexity and scale, AI is emerging as a powerful ally, offering innovative solutions to protect digital assets and infrastructure. At Cerebra, we explore how AI is reshaping the cybersecurity landscape—from enhancing threat detection to automating response mechanisms—and highlight the critical role it plays in building resilient defenses for a constantly evolving threat landscape.
AI-Powered Threat Detection and Prevention
Traditional cybersecurity approaches often struggle to keep pace with the sheer volume and sophistication of modern attacks. AI, with its ability to process vast amounts of data at machine speed and identify hidden patterns, is revolutionizing threat detection. Machine learning algorithms, for instance, can analyze network traffic, user behavior, and system logs in real-time, pinpointing anomalies that indicate malicious activity far more quickly and accurately than human analysts alone.
For example, AI can detect subtle deviations in user login patterns, identify polymorphic malware that frequently changes its signature, and flag suspicious data exfiltration attempts. These proactive capabilities enable organizations to stop threats before they escalate, minimizing potential damage and downtime. The continuous learning nature of AI models means they can adapt to new threats as they emerge, providing an ever-improving layer of defense.
Automating Incident Response and Remediation
Beyond detection, AI is also playing a pivotal role in automating incident response. In a cyberattack, every second counts. AI-powered Security Orchestration, Automation, and Response (SOAR) platforms can automatically execute predefined actions based on detected threats, such as isolating infected endpoints, blocking malicious IP addresses, or revoking compromised credentials. This automation significantly reduces response times, allowing security teams to focus on more complex strategic tasks rather than repetitive manual processes.
This not only enhances operational efficiency but also ensures a consistent and rapid response to incidents, which is crucial in mitigating the impact of fast-moving threats like ransomware or zero-day exploits.

Securing the Human Element: The Phishing Challenge
While AI excels at analyzing data and automating responses, the human element remains a primary target for cybercriminals. Phishing attacks, social engineering, and human error continue to be major vulnerabilities. Even the most advanced AI systems can be bypassed if an employee falls victim to a well-crafted phishing email.
This is where a multi-layered defense strategy becomes indispensable. Alongside AI-powered technical controls, solutions that specifically address human vulnerabilities are crucial. For example, Cerebra’s PhishGuard offers advanced phishing protection, safeguarding organizations against malicious emails and websites that attempt to steal sensitive information. By integrating such specialized tools, businesses can strengthen their security posture to defend against both technical exploits and human-centered attacks.
The Future of Cybersecurity is Intelligent
The integration of AI into cybersecurity is not just an enhancement; it represents a fundamental shift in how we protect digital assets. As AI continues to evolve and mature, we can expect even more sophisticated defense use cases, including predictive security, autonomous defense systems, and highly intelligent threat intelligence platforms. However, this also means that cybercriminals will increasingly leverage AI in their attacks, leading to an ongoing arms race in the digital realm.
For organizations, the key to navigating this intelligent future lies in embracing AI as a core component of their security strategy, investing in continuous learning for their security teams, and adopting integrated solutions that provide holistic protection across all attack vectors. Cerebra is committed to helping businesses build robust, adaptive, and intelligent defenses that can meet the challenges of tomorrow’s cyber landscape.
In conclusion,
the cybersecurity landscape is in a constant state of change, driven by both technological advancements and the ingenuity of cybercriminals. AI stands as a pivotal force in this evolution, offering unprecedented capabilities for threat detection, prevention, and response. As organizations navigate this complex terrain, embracing AI-powered solutions and fostering a culture of continuous learning are essential. Cerebra is dedicated to empowering businesses with the intelligent defenses needed to secure their digital future, ensuring resilience against ever-evolving cyber threats.
Share this article:
Popular

Enhancing Cybersecurity for a Leading Saudi Ministry
A prominent Saudi Arabian ministry has taken significant steps in its digital transformation journey, focusing on strengthening its cybersecurity framework while aligning with the goals of Vision 2030. In the face of challenges like outdated authentication methods, complex access environments, and strict compliance requirements, the ministry embarked on a two-phase solution to address these issues effectively. Phase One: Implementing Cerebra mPass MFA The first phase of the solution introduced Cerebra mPass Multi-Factor Authentication (MFA), designed to offer a more adaptive, user-friendly approach to authentication. This system enables seamless access controls for users while enhancing security through multiple layers of verification. ...
26th May 2025
Revolutionize Enterprise Communication Platform with LinQ2
Revolutionize Enterprise Communication Platform with LinQ2 In today’s fast-paced business environment, enterprise communication platform is the backbone of success. Whether reaching customers, coordinating with employees, or automating notifications, having an effective enterprise communication platform is essential. Cerebra’s LinQ2 stands out as the ultimate solution, offering a multi-channel notification platform tailored for businesses of all sizes. Why Enterprise Communication Platform Is Essential for Business Growth? Efficient enterprise communication platform ensures businesses can stay connected with their customers and teams in real time. Poor communication systems often lead to missed opportunities, customer dissatisfaction, and delays in internal operations. Key Features of LinQ2 ...
11th Mar 2025
Deepfake in Phishing: Challenges and Solutions
In the era of advanced technologies, especially with the explosive adoption of Large Language Models (LLMs) and Generative Artificial Intelligence (GenAI), deepfake has emerged as one of the most significant challenges in cybersecurity. This technology relies on Artificial Intelligence, specifically deep learning and the use of GenAI, to create fake yet highly realistic content that is difficult to detect. Deepfake serves as a versatile tool spanning applications from entertainment to cybersecurity. However, its misuse can pose severe risks, especially in phishing schemes. What is Deepfake? Synthetic media refers to a technology that leverages deep learning algorithms to create ...
19th Dec 2024
AI Governance: Opportunities and Challenges in Cybersecurity
AI Governance: Opportunities and Challenges in Cybersecurity With the increasing reliance on AI technologies in various fields, AI Governance has become a key factor to ensure system integrity and data protection. This governance plays an essential role in enhancing confidence in modern technology and ensuring that it is used responsibly. It has been almost two years since OpenAI’s ChatGPT went viral, igniting widespread interest in artificial intelligence (AI) and setting off a wave of technological and investment growth in the field. Academic and technical investments in artificial intelligence: The advancements in AI since then have been staggering, with exponential increases ...
14th Nov 2024
Cyber Warfare Unveiled: Tracing the Journey from Espionage to Digital Combat
“Cyber Warfare: From Espionage to War A Journey Through Time” With the massive technological advancements, the boundaries of warfare have expanded to encompass cyberspace, where “cyber warfare” has emerged as an increasingly serious threat to individuals, institutions, and countries. The line between cyber and traditional wars has blurred for a while but recent activities in the region made it clear that cyberwars is becoming a dangerous and can lead to harming humans. In this blog, we will dive into a journey through the world of cyber warfare, seeking to understand its nature, history, impacts, types, evolution, and some solutions to ...
9th Oct 2024
Keeping Our Kids Safe Online
A Guide For Keeping Your Kids Safe Online Parents and all who are concerned about the well-being of our young kids in this digital world. Today we will discuss a topic of utmost importance: digital safety for kids. Yes, the Internet can be a very dangerous place for our young kids , especially with the spread of phishing scams. So, let us dive deeper and present to you, in this comprehensive article, a comprehensive guide on digital safety for kids. What every parent needs to pay attention to. Internet risks for kids: The internet has become a big part of ...
17th Jul 2024
Could you be hacked through Slack?
Could you be hacked through Slack? The usage of collaboration platforms such as Microsoft Teams and Slack has significantly increased, with nearly 80% of employees utilizing them. These platforms are designed to be convenient and easily manageable for daily conversations within organizations. However, what makes them easy and convenient also renders them vulnerable to cyber threats and attacks. In 2021, for instance, 780 gigabytes of data from the gaming giant Electronic Arts (EA) were breached through Slack! During the same year, a security vulnerability in Microsoft Teams was exploited to launch a widespread cyber attack on ...
12th Jun 2024
Tips To Be Cyber Protected While Traveling
Goodbye worry! A safe journey in the digital world With all the modern wonders of the digital world, we trust communication technologies on our journeys. There is no doubt that the travel experience is always more beautiful and enjoyable, but it can also pose a range of risks, especially when it comes to cybersecurity. Travelers may fall victim to phishing, Wi-Fi network spying, and theft of their personal data, which can make their journey filled with worries and tension. With the increasing prevalence of cyber threats, it is essential for travelers to follow some guidelines to protect their devices and ...
1st Apr 2024
Push Authentication: A New Era in Multi-Factor Authentication
Want To Say Goodbye To Passwords and OTP Codes? Discover Push Authentication! It is easy for your password to be compromised through phishing attacks, even if it meets the cybersecurity strong password standards and is difficult to predict So we must get to know the technique of Push based Authentication. Some may recommend that you use Multi-Factor Authentication (MFA) to increase your security. Multi-Factor Authentication (MFA): MFA is the process of logging into your account through multiple steps. It requires you to enter more information, not just your password. But there is another obstacle that arises when using such ...
14th Feb 2024