hacker hat colors | Explained
There are different hacker hat colors: black, white, grey, white, green, and blue hats. this article will explain you the deference..

When the word hacker or hacking is mentioned, a universal definition pops into mind. A hacker is known to be a cybercriminal who inflicts chaos on their victims by breaching, stealing, or damaging online systems and data. This is just one part of what the word hacking withholds. And contrary to popular belief, hacking is a broad and diversified category that is misunderstood.
The dependency on storing data electronically, as computers have taken over a large part of our life, results in the increased risk of data theft and becoming suspectable to hacking accidents. So, learning more about the hacking industry and how they operate is crucial to protecting your business, especially with hackers launching attacks every 39 seconds. A simple starting point would be to learn the several types of hackers out there, to the surprise of many there is not only an “evil” hacker but there are also other types of hackers ranging from their intentions and techniques.
What are the 6 of hacker hat colors ?

– Black Hat:
The first color of a hacker hat is black, and they are the most familiarly known to people. black hat hackers are those who are knowledgeable in the cybersecurity industry and use it to their advantage. They are cybercriminals because they access systems and data unauthorizedly with ill intentions to damage or steal either for personal satisfaction or to sell it on the dark web.
These hackers are always looking for vulnerabilities unidentified by the organization so they could take advantage of them. And around 300,000 new versions of malware are being created daily for these purposes. The financial toll these attacks have caused cost the world $600 billion in 2018 and is predicted to rise in numbers this year. More and more cybercrime groups are emerging and following the steps of notorious groups such as Lapsus$, Anonymous, and REvil. These groups have successfully breached and stolen data from many known companies that claim to have a secure cyber system, but 73% of black hat hackers claim that “traditional firewall and antivirus security is irreverent or obsolete” and 80% said that humans are their gateway to systems due to their repetitive mistakes.
– White Hat:
Next, are white hat hackers who contrast black hats. Just like in American western movies, black hats represent the villains and white hats represent the heroes. White hat hackers use their knowledge in cybersecurity for different purposes. They are professionals who are paid to breach and hack a company’s system to assess their organization’s level of cybersecurity and, as a result, discover and correct weak points to avoid attacks from external threats.
They are ethical hackers who oversee protecting the company’s systems from Black hat hackers. In 2018 white hats made up to $19 million in commission for helping organizations discover vulnerabilities in their systems (The 2019 Hacker report by Hackerone). And with an alarming number of 62%, many businesses are ill-equipped to protect themselves from any cyber threats (IBM Cost of a Data Breach Report 2021). This will only damage the company and cost them up to millions of dollars to revive their systems.
– Grey Hat:
The next color falls between black and white. Grey hat hackers don’t fall in a specified category in terms if they are villains or heroes, they share the same technical skills, but their intentions vary. These types of hackers don’t have ill intentions such as black hats, they do exploit vulnerabilities but not with the end goal of destructing the system, but due to their fascination with the hacking world and the desire to improve their skills. Nonetheless, they are significantly different than white hats due to them illegally finding loopholes and weak points in systems for their own satisfaction. Globally, around 4.6% of cyber security professionals have taken on the role of a grey hat hacker while on the job, and 41% know one. These numbers prove the existence of such hackers and how all hacker’s intentions differ from each other.
– Blue Hat:
The fourth hat color is Blue. These types of hackers separate in to two, first are those who use their limited hacking skills for revenge. Their objective is to shut down a specific target for vengeance and then stop after achieving it. Unlike black hatters, they don’t continuously launch attacks since they are not doing so for financial gain, only to gain favorability.
Second, are those who are scouted by companies to be penetration testers on new unreleased systems to look for any vulnerabilities missed. They launch attacks without causing any harm to the systems. Microsoft holds BlueHat conferences where they invite hackers to discuss with Microsoft engineers their current cyber threats and to test out Windows programs.
– Red Hat:
The following color is a red hat hacker, also known as the vigilantes of the cyber world. They strive with the mission to keep black hat hackers under control by launching targeted attacks on them and destroying their systems and resources. Their approach is aggressive and merciless, and they don’t seek help from officials or report the cybercriminals they find. They believe in their capabilities to reach their objective of stopping them black hat hackers from attacking again.
– Green Hat:
Lastly, are green hat hackers. They are wannabe black hats. While they do lack the set of skills and experiences as black hat hackers, they still are a threat as they are learning to strive in this industry. They are typically known as those who want to be acknowledged for their skills which is why they attack businesses with limited security. These green hat hackers are black hats in the making.
In conclusion
For many people, a hacker is a person who intrudes systems unauthorizedly and steals confidential information or destroys them. But now this has changed. There are different hat colors for the different intentions of hackers. At first, it was black and white but now the colors have diversified. And understanding the several types of hackers, as well as hacker hat colors, is essential for cybersecurity professionals and security departments as hacking and hackers are undoubtedly the most significant threat for any company.
Also Read: Recent Phishing Attacks in Saudi Arabia|2020
Be up to date with the cybersecurity industry!
Share this article:
Popular
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means
Major Data Leak Exposes 183 Million Email Accounts – What Happened and What It Means A massive data leak came to light on October 28, 2025, with reports confirming that hundreds of millions of user credentials have been exposed online. Below, we break down the key facts of this breach – including its source, scale, and implications – and then explore how cybersecurity solutions from Cerebra.sa could help prevent or mitigate such incidents in the future. Overview of the October 28, 2025 Data Leak Source/Target: The breach did not stem from a single company hack, but rather from a trove ...
29th Oct 2025
Top 3 Phishing Types and How to Prevent Them in 2025
Phishing Types: Spear Phishing, Smishing & How to Avoid Phishing Emails The Enduring Threat of Phishing Phishing types like spear phishing, smishing, and whaling are becoming more sophisticated in 2025, making it harder than ever to avoid phishing emails. This guide explores the most dangerous phishing types and shows you how to recognize and prevent them before they cause harm. The National Cybersecurity Authority (NCA) reinforces this urgency with its awareness message: ‘Stop for 5 seconds… Guard Your Cyberspace.’ What Is Phishing? Phishing is a cyberattack where malicious actors impersonate trusted entities—like banks, government agencies, or delivery companies—through emails, ...
5th Aug 2025
5 Benefits of Using AI in Cyber security | Artificial Intelligence
Using AI in Cybersecurity We should start learning using AI in cyber security because Hackers aren’t going to slow down any time soon and with a using AI! The next step to level up in protecting your business’s IT infrastructure is to integrate artificial intelligence. Studies have revealed that AI will strengthen the wall between systems and cyber threats. According to an IBM report, the average total cost of a data breach increased in 2021 from $3.86 million to $4.24 million. Cybercriminals are becoming more sophisticated and advanced in their attacks resulting in this significant rise in cost. They are elevating ...
1st Aug 2025
6 benefits of SMS Marketing you should know!
6 benefits of SMS Marketing you should know! Have you ever used SMS marketing to reach and communicate with your audience, if not! I’m sure that you will change your mind when you read about the benefits of SMS Marketing, continue this article to learn.. Many businesses are constantly seeking ways to interact with and attract new customers. Their joint objective is to reach a wider audience. To do so, communication is key. There are many ways for businesses to communicate with their audience, either by email, social media, or adverts, but the most beneficial marketing method, that is often ...
30th Jul 2025
MFA: the New Firewall In the 21st century
MFA- Multi Factor Authentication This article will help you to understand why Multi Factor Authentication( MFA )became an important architectural component in protecting us in the new Working From Home. Introduction In the early days, Cybersecurity (then called IT Security or information security) used to be merely a username and password. If you ask to someone, they would say I have a username and password so I am safe. It wasn’t much of the internet at that time. Eventually, people have learned that password isn’t sufficient to protect their digital assets. So Antivirus (AV) software flourished and we saw a ...
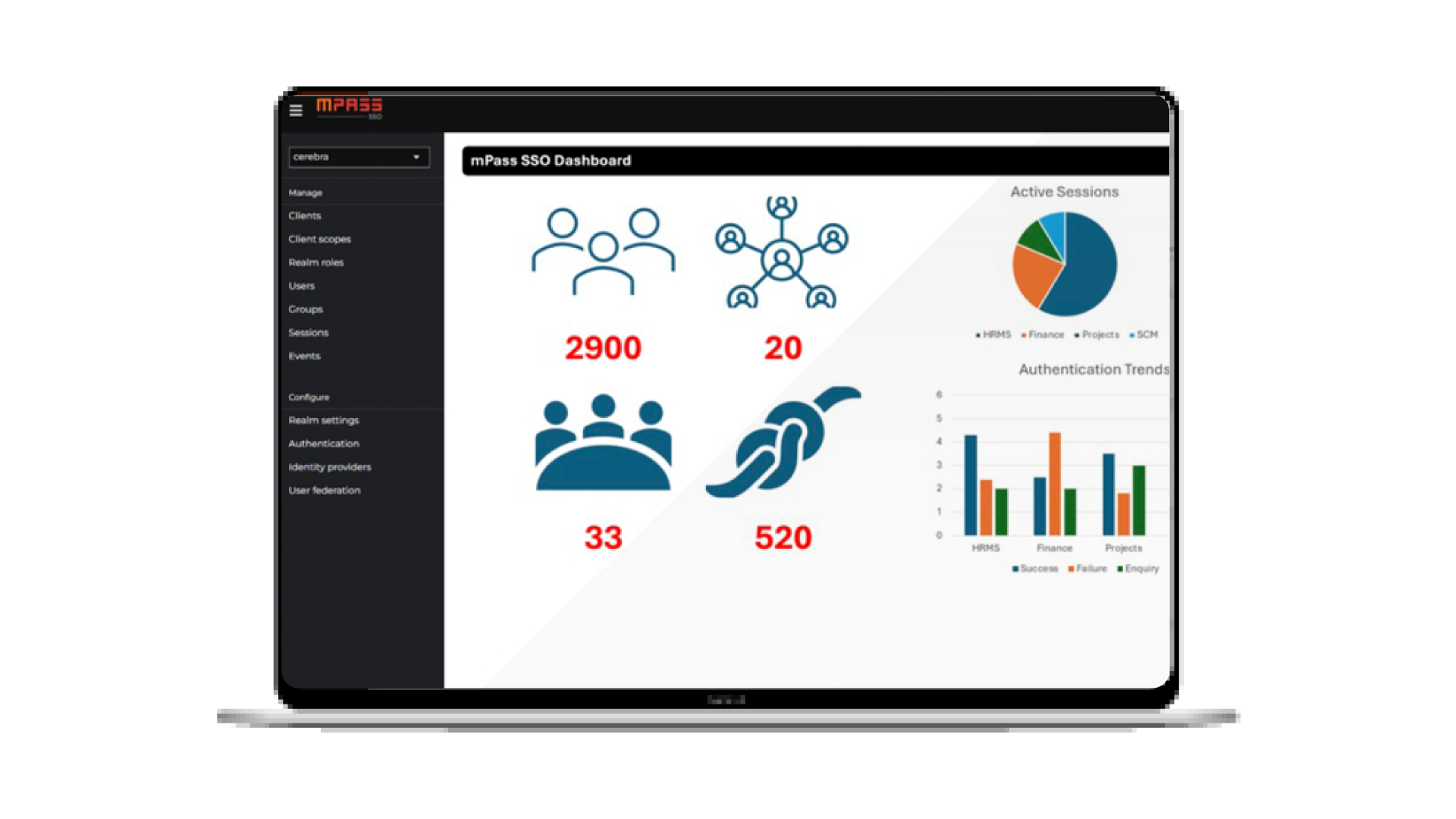
20th Jul 2025
What is the role of MFA? |ECC & SAMA Compliance
ECC & SAMA Compliance with MFA solution Do you know that there are a great MFA solutions in market today help your organization for ECC & SAMA Compliance? this article will show you how and we will provide you the most incredible MFA solution help to comply with Cybersecurity regulation in KSA.. With the world of cyber threats becoming more intense than ever, organizations need to comprehend the need for an improved cybersecurity framework. The universal goal is to protect the organization’s network from any outsider or insider threats, especially with the addition of remote work resulting from the COVID-19 ...
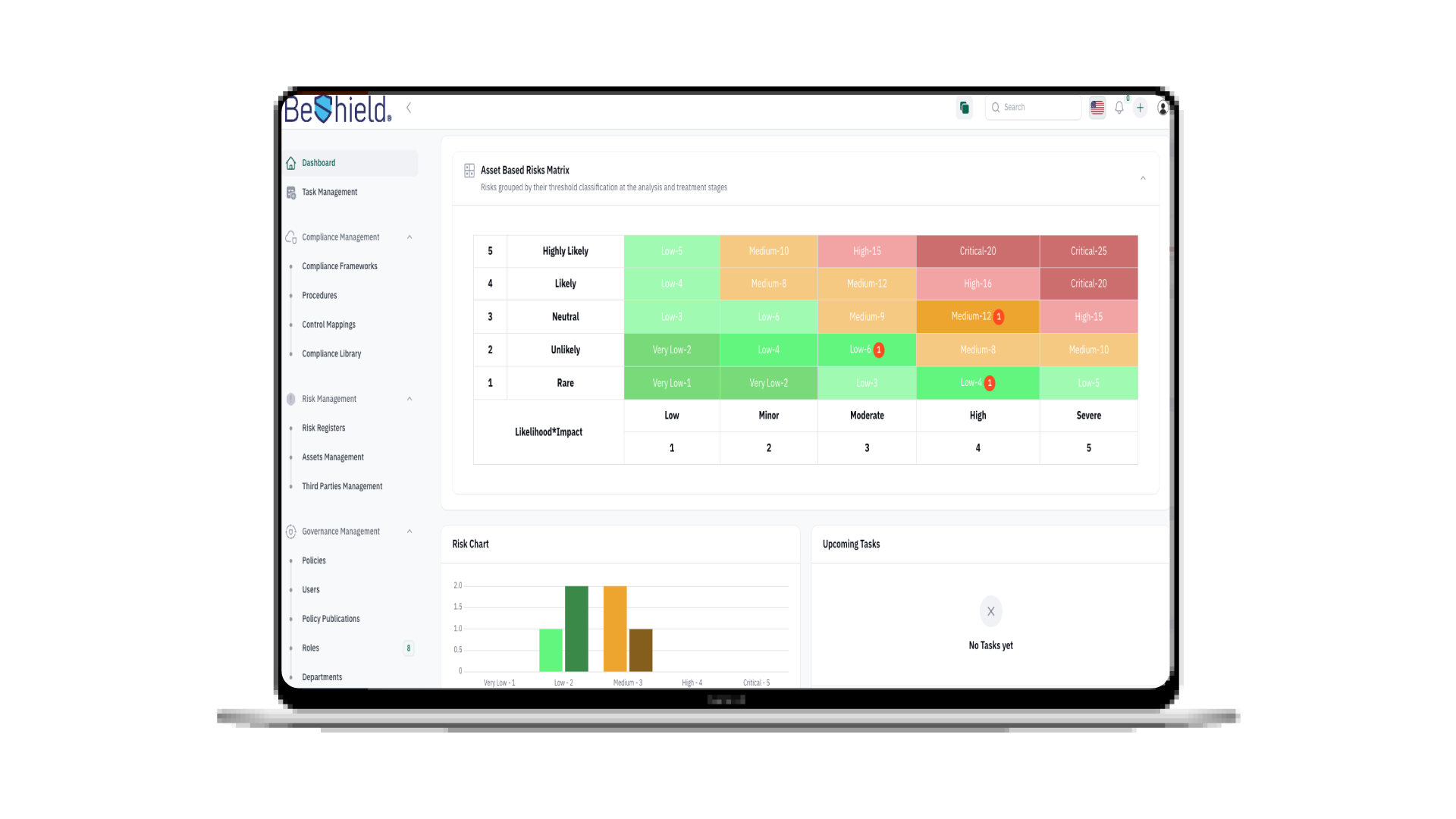
15th Jul 2025
The AI Revolution in Cybersecurity: A New Frontier of Defense
The AI Revolution in Cybersecurity: A New Frontier of Defense How is AI revolutionizing the cybersecurity industry? The rapid evolution of Artificial Intelligence (AI), especially with the rise of Generative AI (GenAI), is not just reshaping every industry; it is fundamentally transforming how we approach digital defense. As cyber threats grow in complexity and scale, AI is emerging as a powerful ally, offering innovative solutions to protect digital assets and infrastructure. For a full list of advantages, read about the 5 Benefits of Using AI in Cyber security. At Cerebra, we explore how AI is reshaping the cybersecurity landscape—from enhancing ...
6th Jul 2025
Uber security breach by 18-year-old Hacker!
Uber security breach by 18-year-old Hacker! Uber security breach proves that the largest companies can be hacked by teenagers! this news will undoubtedly shock you.. How Uber security breach happened? Uber recently experienced a cyberattack where an 18-year-old hacker accessed their systems by launching a successful social engineering attack on an employee. The hacker used stolen employee credentials to launch an MFA (Multi-Factor authentication) Fatigue attack. It is an attack where a victim receives multiple requests from their MFA application till it bothers them out leading them to eventually accept the request. The teenage attacker did not disclose how he ...
15th Jun 2025
Biometric Authentication: Is it reliable?
Biometric Authentication The history of bio-metrics used as an authentication tool dates to the 1800s. It was first used by the French to identify criminals through their fingerprints, which later the English police commissioner, Edward Henry, developed HCS “Henry Classification System”. It was a system that relied on fingerprints to identify people who have been prosecuted, it was a prime way of classification used by the police during the 20th century. As the years continued, new biological traits started being used in biometric authentication which in result are replacing traditional methods of authentication. Any invention introduced in the cyber world ...
10th Jun 2025